In a few recent video blogs, the Protected Trust team has discussed the issue of phishing and how it affects companies of all sizes. In these videos, we showcased a few different examples of email phishing that have succeeded before.
What is phishing? How can you prevent phishing attacks from working? Here’s a quick explanation of this cyber threat, and some of the things that you can do to curtail it:
What is Phishing?
Phishing is a type of social attack strategy where an attacker sends their target a message to goad them into taking some kind of action. This can include tricking victims into downloading malware, sharing sensitive information, surrendering account credentials, and more.
The problem with phishing is that it comes in many forms. Some types of phishing attacks include:
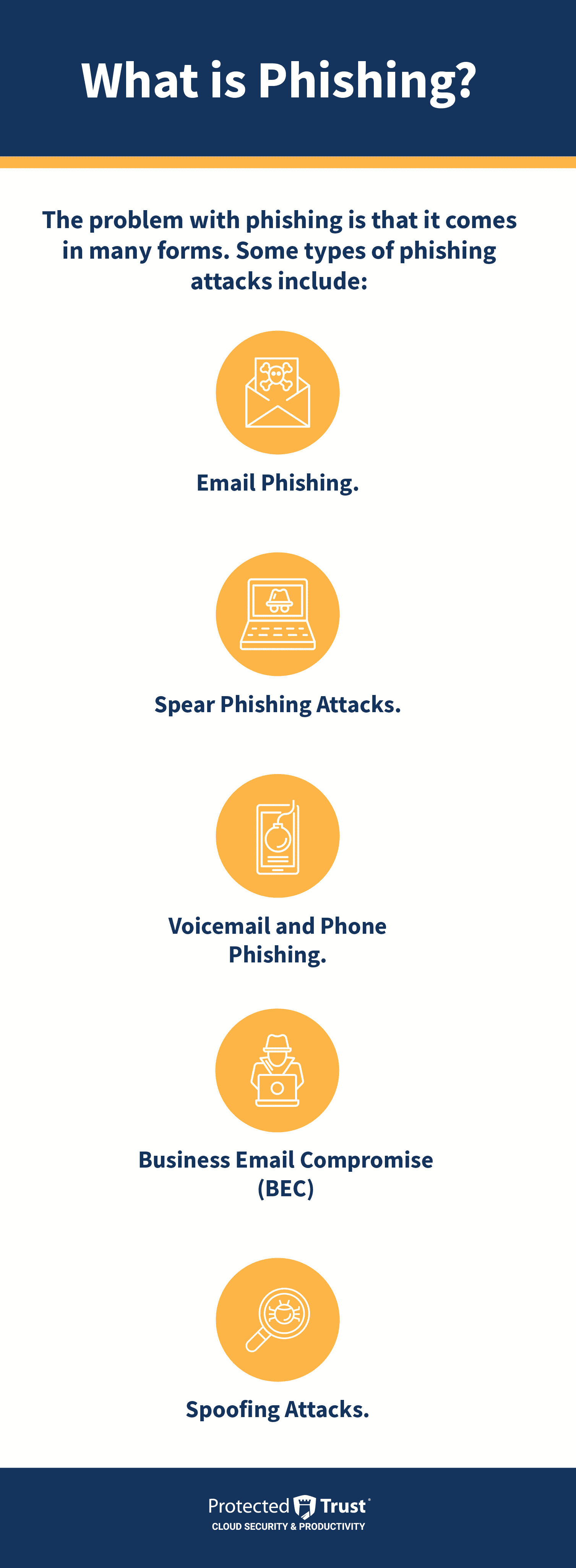
- Email Phishing. A primary method of phishing involves sending fraudulent phishing emails that mimic legitimate communications from a well-known company or an anonymous “friend.” Here, the goal is often to get the victim to download a malicious file or visit a fake version of a website to capture their login information.
- Spear Phishing Attacks. Where many phishing attacks use generic urgency language sent out to as many targets as possible, some phishers put in more effort to learn about a specific target. Spear phishing attacks take more care to mimic someone within an organization or a vendor that the organization partners with to make their fake communications seem more genuine. These attacks are highly targeted, and may leverage information collected about the target from other sources (social media, company bio pages, leaked data on the dark web, etc.) to maximize their effectiveness.
- Voicemail and Phone Phishing. Voice-based phishing attacks (or vishing) where a malicious actor (or a recording from them) communicates via phone messages to trick their target. A common example of this would be a phone call with a recorded message asserting that the recipient is under investigation by the IRS and owes $500 or some other amount, then provides instructions to submit a check or (more ridiculously) a gift card to the IRS by a set date or face consequences. Note that the IRS doesn’t demand immediate payment with specific payment methods over the phone—they would send a written bill first. Also, payments would be made to the United States Treasury, not the IRS.
- Business Email Compromise (BEC). A specific form of phishing where the attacker poses as a higher-up in the company—typically a CEO—and sends a phishing email to someone within the company. This type of email phishing relies on the target not wanting to question “orders from above.” Phishing attacks using BEC tactics are often geared towards approving fake invoices or stealing sensitive data and credentials.
- Spoofing Attacks. Some phishing attacks leverage “spoofing” techniques to make them more effective. Spoofing is when an attacker changes some of the information in their communication to make it look like it came from a legitimate source. For example, spoofed email addresses might be made to look like the email address of a legitimate sender, or vishing calls might use a spoofed phone number to look like they’re coming from a legitimate business or government agency. These aren’t attacks in and of themselves—just a way to make other attacks more convincing.
These are just a few examples of different types of phishing campaigns that attackers may launch. Also, it’s important to note that these strategies aren’t mutually exclusive by any means—attackers may use multiple methods to increase their likelihood of success.
For example, someone sending a spear phishing email might also try to pose as a CEO in the organization (a BEC tactic) to make their attack more effective. Combined with email spoofing, this hypothetical phishing attack would look remarkably like the real thing—especially if the attacker took the time to recreate or copy the company letterhead and insert it into the email.
As time goes on, phishing attacks will only grow more prevalent and sophisticated—gone are the days of the obviously-fake Nigerian Prince emails.
How Can I Prevent Phishing Attacks?
Phishing attacks will probably never stop. They simply work too well for attackers to abandon the strategy. Case in point: according to data cited by the Federal Trade Commission, “people lost $30 million to phishing schemes in one year.” Also, the Internet Crime Report for 2017 shows that BEC/EAC attacks (which they track separately from normal phishing) resulted in over $671 million in losses.
Even with training to prevent people from falling victim to fake emails, there’s still a high risk that someone in your company will get tricked by one. As Steve Goodman said in a vlog on the subject, even with training, about “15 percent [of your employees] would still click on a phishing email.” Part of the problem is that many employees still think that phishing emails are going to be as obvious as the Nigerian Prince example. They’re not.
While you won’t stop cyberattacks like phishing from happening, you can reduce your risk by following a few simple precautions.
- Providing Training in Modern Phishing Techniques. Sure, training won’t stop phishing attacks, but it can reduce the odds of an employee falling for a phisher. Sometimes, simply being aware of a cyber threat is enough to promote better threat management. However, this should never be the only precaution you take.
- Leverage Email Encryption and Authentication. Email encryption and authentication tools can make it much easier to identify spoofed emails. For example, in Microsoft Office 365, admins can enable organization-wide email encryption. When users get an encrypted email, there will be an indicator on it that proves that the email had the appropriate encryption. An icon showing that an email was not encrypted properly can serve as a red flag for a potential phishing attack.
- Use Advanced Threat Protection (ATP) Features. Some business productivity solutions, such as Microsoft Office 365, offer advanced threat protection features that can help to detect and counteract phishing emails. By checking source domains, links, and file attachments before employees click on anything, Microsoft’s ATP solution can help identify potential dangers and keep employees from accidentally falling for phishing attacks.
- Set Policies for Verifying Sender Identities. Instead of having employees blindly accepting all requests that hit their inbox, consider setting policies and procedures for having employees verify who sent that email or text before they follow any directions in it. For example, instead of responding to an email directly by hitting “reply,” have employees create a new email and send it to the person in question directly to verify that the first communication was legitimate. This can help to curtail email spoofing and BEC attacks.
These are just a few tips for managing the threat posed by phishing emails. Need help setting up cybersecurity measures to counter phishing? Reach out to the Protected Trust team to get started!
{{cta(’31e53ad0-858c-4b4b-b6a2-00da4238bf2f’,’justifycenter’)}}