What is Phishing and How Can You Stop It?

In a few recent video blogs, the Protected Trust team has discussed the issue of phishing and how it affects companies of all sizes. In these videos, we showcased a few different examples of email phishing that have succeeded before.
Real-World Examples of Ethical Phishing Emails
In a recent video blog, I sat down with Sean Jacobs to discuss a real-world example of a phishing email that he had turned into a training opportunity. Using that email, he could showcase to clients how easy it is for employees to fall victim to a phishing scam.
How do Hackers Get Your Business Information?

Everyone knows what a cyber attack is. After all, we constantly hear about data breaches and cybersecurity threats in the news. But how do hackers actually execute these attacks? In this video and corresponding blog post, Security Architect Sean Jacobs explains just how easy it is for hackers to gain entry into most businesses—plus how […]
Wargame your own company with Phishing Attack Simulator
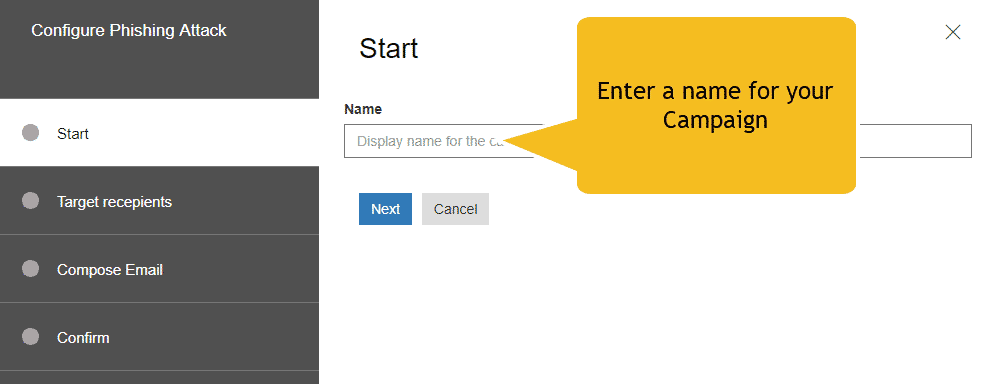
With Attack Simulator (included in Office 365 Threat Intelligence), if you are a member of your organization’s security team, you can run realistic attack scenarios in your organization. This can help you identify and find vulnerable users before a real attack impacts your bottom line.
How Measuring Security for Risk ROI Can Empower CISOs
For the vast majority of business decisions, organizations seek metrics-driven proof. Why is cybersecurity the exception?
Email Phishing Has Never Been Easier


