With Attack Simulator (included in Office 365 Threat Intelligence), if you are a member of your organization’s security team, you can run realistic attack scenarios in your organization. This can help you identify and find vulnerable users before a real attack impacts your bottom line.
The Attacks
At preview release we offer 3 kinds of attack simulations that you can run.
For an attack to be successfully launched, the account that is running the attack and logged on, must use multi-factor authentication.
Note: Currently, Attack Simulator is in preview.
When an attack is created, the attack email message is created using HTML via a text field. However, when Attack Simulator is generally available, the email will be created using an HTML control within the experience. Also, the landing page a target is redirected to in a Spear Phishing campaign is static. However, when Attack Simulator is generally available, the landing page will use a customizable URL chosen by the global or security administrator configuring the simulated attack.
To access Attack Simulator, in the Security & Compliance Center, choose Threat management > Attack simulator.
Before you begin…
Make sure that you and your organization meet the following requirements for Attack Simulator:
Display name spear-phishing attack
Phishing is a generic term for a broad suite of attacks classed as a social engineering style attack. This attack is focused on Spear Phishing, a more targeted attack that is aimed at a specific group of individuals or an organization. Typically, a customized attack with some reconnaissance performed and using a display name that will generate trust in the recipient, such as an email message that looks like it came from an executive within your organization.
This attack focuses on letting you manipulate who the message appears to have originated from by changing the display name and source address. When spear-phishing attacks are successful, cybercriminals gain access to users’ credentials.
To simulate a spear-phishing attack
- In the Security & Compliance Center, choose Threat management > Attack simulator.
- Specify a meaningful campaign name for the attack.
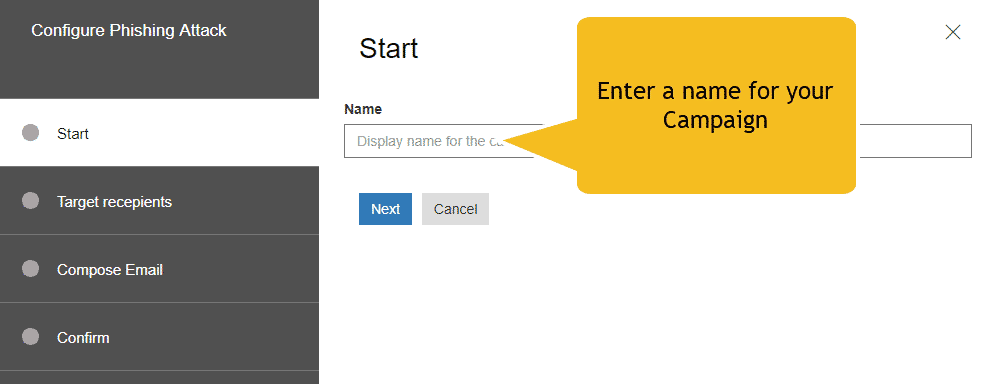
- Specify the target recipients. This can be individuals or groups in your organization. A targeted recipient must have an Exchange Online Mailbox in order for the attack to be successful.
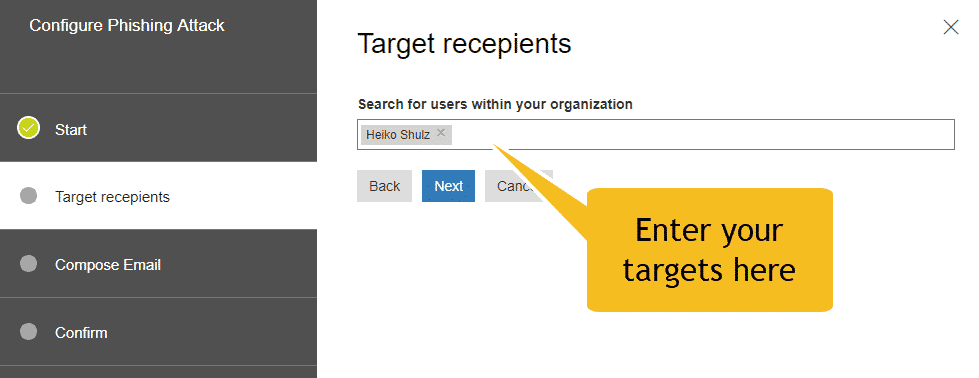
- Compose the phishing email message.
- Enter text for the From (Name) field. This is the field that shows in the Display Name in the receiving email client.
- Enter text or the From field. This is the field that shows as the email address of the sender in the receiving email client.
Important: You can enter an existing email namespace within your organization (doing this will make the email address actually resolve in the receiving client, facilitating a very high trust model), or you can enter an external email address. The email address that you specify does not have to actually exist, but it does need to following the format of a valid SMTP address, such as user@domainname.extension.
- Using the drop-down selector, select a Phishing Login server URL that reflects the type of content you will have within your attack. Several themed URLs are provided for you to choose from, such as document delivery, technical, payroll etc. This is effectively the URL that targeted users are asked to click.
- Enter text for the Subject field. This is the field that shows as the Subject Name in the receiving email client.
- Next enter the content for the Email body that the target will receive. This content must in HTML format. You can craft the HTML directly in the Email body field itself or cut and paste from another HTML editor. There are two important fields for inclusion in the HTML:
The HTML formatting can be as complex or basic as your campaign needs. As it is HTML, you can insert images and text to enhance believability. You have control on what the received message will look like in the receiving email client.
- Choose Finish to launch the attack. The Spear Phishing email message is delivered to your target recipients’ mailboxes.
Password-spray attack
A password spray attack against an organization is typically used after a bad actor has successfully enumerated a list of valid users from the tenant, utilizing their knowledge of common passwords used. It is utilized widely as it is a cheap attack to run, and harder to detect than brute force approaches.
This attack focuses on letting you specify a common password against a large target base of users.
To simulate a password-spray attack
- In the Security & Compliance Center, choose Threat management > Attack simulator.
- Specify a meaningful campaign name for the attack.
- Specify the target recipients. This can be individuals or groups in your organization. A targeted recipient must have an Exchange Online Mailbox in order for the attack to be successful.
- Specify a password to use for the attack. For example, one common, relevant password you could try is Fall2017. Another might be Spring2018, or Password1.
- Choose Finish to launch the attack.
Brute-force password attack
A brute-force password attack against an organization is typically used after a bad actor has successfully enumerated a list of key users from the tenant. This attack focuses on letting you specify a set of passwords against a single user.
To simulate a brute-force password attack
- In the Security & Compliance Center, choose Threat management > Attack simulator.
- Specify a meaningful campaign name for the attack.
- Specify the target recipient. A targeted recipient must have an Exchange Online Mailbox in order for the attack to be successful.
- Specify a set of passwords to use for the attack. For example, one common, relevant password you could try is Fall2017. Another might be Spring2018, or Password1.
- Choose Finish to launch the attack.